September 2013
We live in a world in which cybercrime is on the rise. Security now, by necessity, must protect all aspects of the enterprise, from the data centre to the desktop and beyond the network edge. Seemingly commonplace, yet still nascent, innovations such as cloud services and the bring-your-own-device (BYOD) trend have only accelerated the need for relevant security at all points in the information lifecycle. Here are six emerging trends and top concerns:
1. Connected societies:
Technology is having a greater influence on society, as seen by the Arab Spring of 2011. And many anticipate that an additional 1 billion people will be online by 2020, with a significant percentage of them from developing countries. “At some point in the near future we will end up with more people having access to the Internet than access to clean water,” says Martin Sadler, director, Cloud and Security, HP Labs. “If you equip people to be a part of this global communications infrastructure when their other needs are not being met, they will turn to the Internet to get access to what they need.”
Kinetic warfare or cyberterrorism has the potential to be an effective means for emerging countries to challenge the developed world on an increasingly level technology playing field. “It is important to think beyond software and system vulnerabilities and understand the wider backdrop that is likely to shape online activity,” says Sadler.
2. Medical device as vulnerability:
Physical security is coming under scrutiny as an increasing number of implanted electronic devices such as insulin pumps and pacemakers are being exposed as vulnerable to hacking. Routinely monitored and interconnected with other devices over wireless networks, they are raising red flags in the security and medical communities as the newest vulnerability due to a lack of regulation and industry oversight. Imagine being held for ransom by someone you never see, who forces you to drain your bank account in exchange for keeping your pacemaker running.
3. The increase in machine-to-machine interactions:
As cities adopt smart grid technologies and buildings become more “intelligent,” breaches in security of these interconnected systems will have a cascading effect. Network grids that control traffic lights, railroad crossings and toll bridges, for instance, could become prime targets for terrorists or hackers looking to extort money from governments or individuals.
4. Our desire to be mobile:
Mobile devices, from smartphones and tablets to laptops and ultrabooks, have become primary sources of communication and information. As a result, web-based applications are proliferating. But how many of them are secure? “Web applications are becoming the preferred method of attacks because they often have vulnerabilities that can be exploited,” says Rebecca Lawson, director, Worldwide Enterprise Solutions Marketing, HP. “Everyone wants to have a cool web app but they don’t know the potential risks and liabilities based on how that app interacts with other apps. These days, security is still, too often, an afterthought.”
5. The increase of cloud services:
As companies move more of their infrastructure and their data to the cloud, adversaries will be able to take advantage of the trend. “In theory, the cloud services model strengthens security because data will be handled by companies with whole teams that think about nothing but security. But we’re not there yet,” says Joseph Menn, author of Fatal System Error: The Hunt for the New Crime Lords Who are Bringing Down the Internet and an investigative reporter with Reuters specializing in cyber security.
6. The growing importance of Big Data:
For large organisations, keeping up with both the volume and the velocity of information is a huge undertaking. Attackers can exploit immense, distributed Big Data systems, which often have limited security controls, and gain access to tremendous amounts of information at once.
In preparation
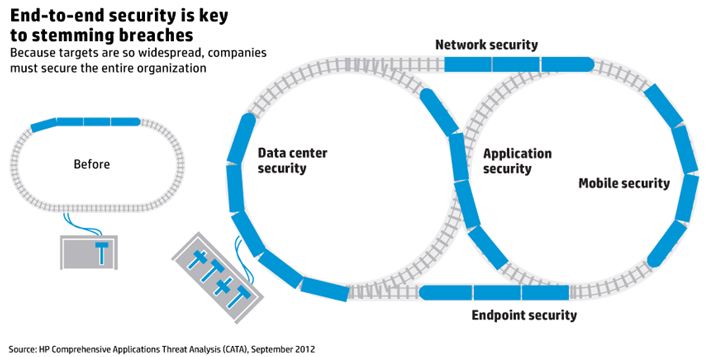
In 2020, companies and individuals alike will need to approach security from a holistic mindset as threats to corporate, government and personal information increase. Security professionals will find themselves answering to CEOs and corporate boards as their policies, processes and vulnerabilities become companywide priorities. In order to reduce technical debt downstream and decrease unplanned downtime, intrusions and business disruption, enterprises will need to embrace a three-step approach to security:
1. Build it in.
2. Make it intelligent.
3. Protect what matters.
The game is no longer about locking down the network and blocking every threat. To compete against adversaries who are increasingly sophisticated and well-funded — and in many cases, unknown — companies have to manage the risk that is inherent in doing business in a connected world.
Enterprise 20/20 is a collaborative effort to imagine the enterprise of the future. There are many ways to get involved:
- Read Security 20/20 for more perspectives on the future of enterprise security.
- Listen to HP’s Art Gilliland on security threats we will face tomorrow.
- Learn about related technology trends at www.enterprise2020.com.
- Discuss these issues with other thought leaders in the Enterprise 20/20 Community.
- Visit the Enterprise 20/20 blog and track the trends of the decade ahead.
Source: http://h30458.www3.hp.com/ww/en/ent/6-security-trends-to-prep-for-now_1330640.html
