Yesterday marked the one year countdown for the end of extended support for Windows XP Service Pack 3 (SP3). I wanted to pause today and lay out some of the important security implications of end of support so that customers are informed about what this change means to them.
It has been twelve years since the release of Windows XP and the world has changed so much since then. Internet usage has grown from ~361 million to more than 2.4 billion users. We have witnessed the rise of the internet citizen with members of society connected through email, instant messaging, video-calling, social networking and a host of web-based and device-centric applications. As the internet becomes more and more woven into the fabric of society, it has also become an increasingly popular destination for malicious activity (as evidenced in the Microsoft Security Intelligence Report.) Given the rapid evolution, software security has had to evolve to stay ahead of cybercrime. To help protect users from rapid changes in the threat landscape, Microsoft typically provides support for business and developer products for 10 years after product release, and most consumer, hardware, and multimedia products for five years after product release.
Per our long established product support lifecycle, after April 8, 2014, Windows XP SP3 users will no longer receive new security updates, non-security hotfixes, free or paid assisted support options or online technical content updates. This means that any new vulnerabilities discovered in Windows XP after its end of life will not be addressed by new security updates by Microsoft. Moving forward, this will likely make it easier for attackers to successfully compromise Windows XP-based systems using exploits for unpatched vulnerabilities. In this scenario, antimalware software and other security mitigations are severely disadvantaged and over time and will become increasingly unable to protect the Windows XP platform.
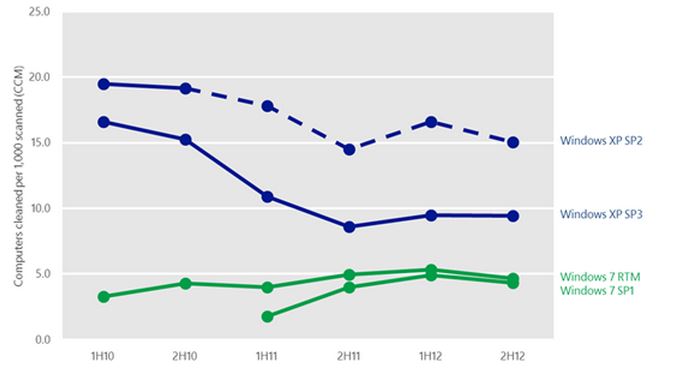
We can get insight into what happens to malware infection rates once a platform goes out of support by looking at Windows XP Service Pack 2 (SP2) as an example. Support for Windows XP SP2 ended on July 13, 2010. Although this platform benefited from numerous security enhancements when it was released, today it has a much higher malware infection rate than Windows XP SP3 or any of the newer Windows operating systems. As the figure below illustrates, computers running Windows XP routinely experience a significantly higher malware infection rate than computers running any other supported version of Windows. Much of the elevated infection rate on Windows XP can be attributed to the fact that some of the key built-in security features included with more recent versions of Windows are not present in Windows XP. Windows XP, designed in a different era, simply can’t mitigate threats as effectively as newer operating systems, like Windows 7 and Windows 8.
Figure 1: Infection rate (CCM) trends for Windows XP SP2 and SP3, Windows 7 RTM and SP1, first half of 2010 (1H10) to second half of 2012 (2H12)
As the threat landscape has evolved over the past twelve years since the release of Windows XP, so has software security. There are many new security features today in more modern operating systems that can better protect users from criminal activity including:
- Kernel improvements: Recent versions of Windows include a number of security-related improvements to the Windows kernel, including:
- Address Space Layout Randomization (ASLR): Introduced in Windows Vista, ASLR randomizes the memory locations used to load core processes, making it more difficult for attacks that target processes by addressing predictable memory locations to succeed.
- Structured Exception Handler Overwrite Protection (SEHOP): Introduced in Windows Vista SP1, SEHOP prevents exploits from overwriting exception handlers to gain code execution by verifying that a thread’s exception handler list is intact before allowing any of the registered exception handlers to be called. For application compatibility reasons, SEHOP is disabled by default on client versions of Windows, but can be enabled by setting a registry key.
- Data Execution Prevention (DEP): Data Execution Prevention is a Windows feature that enables the system to mark one or more pages of memory as non-executable, making it harder for exploits involving buffer overruns to succeed. Originally introduced with Windows XP SP2, DEP is enabled by default in Windows 8, enhancing security out of the box.
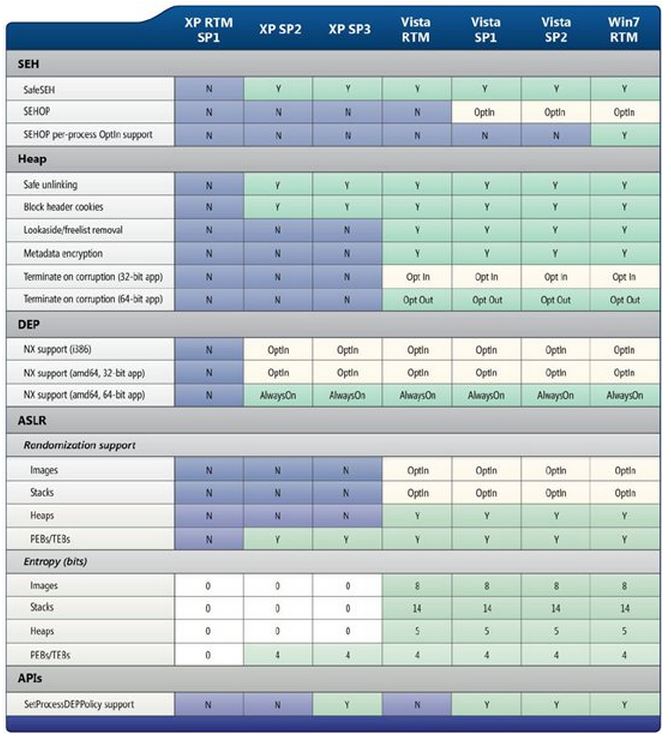
Figure 2: Availability of exploit mitigations on Windows client SKUs (Windows XP – Windows 7) as published in The SDL Progress Report
- Real-Time Malware Protection: In Windows 8, Windows Defender provides real-time protection against malware and potentially unwanted software out of the box.
- BitLocker Drive Encryption: Introduced in Windows Vista, BitLocker Drive Encryption enables users and administrators to encrypt entire hard drives, protecting data on lost or stolen computers from unauthorized access. Windows 7 introduced BitLocker To Go, providing full disk encryption for removable volumes. In Windows 8, BitLocker can more easily be deployed and managed.
- User Account Control (UAC): Introduced in Windows Vista, User Account Control helps prevent unauthorized changes to a computer by enabling user accounts to run without administrator permissions except when needed to perform administrative tasks. UAC was streamlined in Windows 7 and later operating systems, providing an improved user experience.
- AppLocker: Introduced in Windows 7, AppLocker can be used by IT departments to restrict the programs users can execute by defining powerful and flexible rules. In Windows 8, administrators can restrict Windows Store apps in addition to legacy Windows applications.
- UEFI Secure Boot: Introduced in Windows 8, UEFI Secure Boot is a hardware based feature that is required on all Windows 8 certified devices. It helps prevent unauthorized operating systems or firmware from running at boot time by maintaining databases of software signers and software images that are pre-approved to run on the individual computer.
- Trusted Boot: The Trusted Boot feature in Windows 8 verifies the integrity of Windows startup files, and includes an Early Launch AntiMalware (ELAM) capability that enables the antimalware software to start before any third party software. By starting the antimalware solution early and within the protected boot process, the operation and integrity of the antimalware solution can be better guaranteed. As part of the boot process, Windows also runs Measured Boot, which allows third-party software on a remote server to securely verify the security of every startup component in a way that would be very difficult for malware to forge. If any tampering with the Windows boot process or the antimalware’s ELAM driver is detected, Trusted Boot will repair the system by restoring the original files.
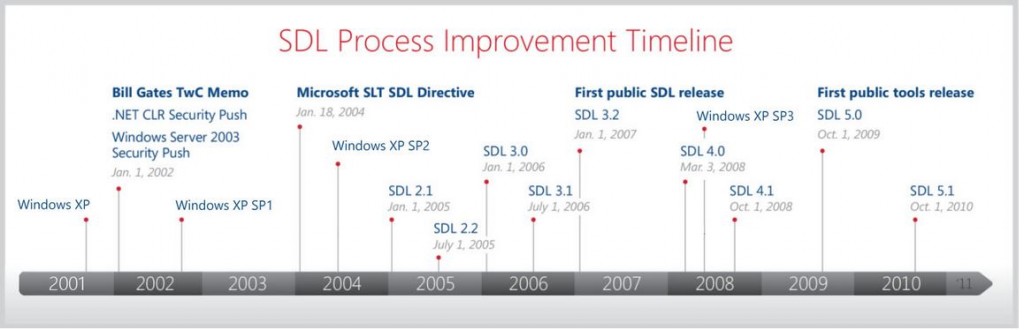
Over and above all the security mitigations and features that are available in more modern operating systems, security development practices have also evolved greatly over the past decade. Figure 2 illustrates some of the major milestones in the evolution of the Microsoft Security Development Lifecycle (SDL) between 2002 and 2010. A detailed list of the specific ways the SDL evolved during this time is available in the SDL Progress Report. Since the SDL is a living methodology, it has continued to evolve beyond the period in the timeline below to the present day.
Figure 3: Timeline of major milestones in the evolution of the SDL at Microsoft as published in The SDL Progress Report
Windows XP was a great operating system in its time and provided value to a large number of people and organizations around the world for over a decade. But all good things must come to an end. I hope this information reinforces the importance of migrating to a modern operating system with increased protections, and instills a sense of urgency onto organizations that are behind schedule on their migration projects. For more information of end of lifecycle support for Windows XP SP3, I encourage you to check out the Windows for your Business blog.
Tim Rains
Director
Trustworthy Computing
