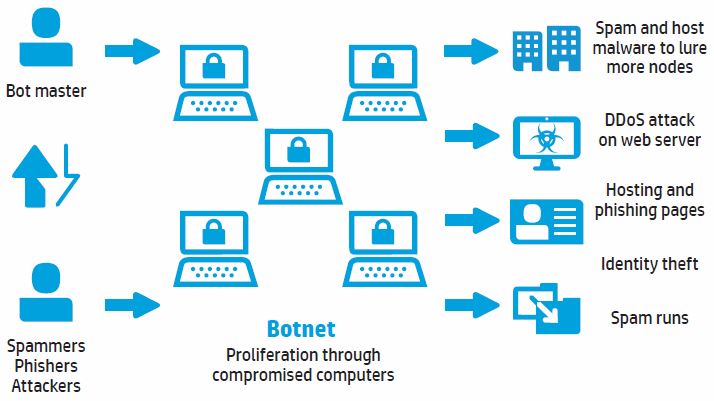
The bot threat –
Today enterprise networks can be attacked in a number of ways. None are more daunting than the Internet robot or simply, the bot. Bots are malicious code programs that are automated to infect a computer network. They can strike in so many different ways that traditional network security is often ineffective in blocking their destructive payloads. Bot infection methods include the downloading of a virus-infected program, infection via a worm, or more sophisticated methods such as a “drive-by” infection, in which users can self-inflict their systems by simply visiting a website. Since bots are self-propagating, they spread exponentially because each bot, in turn, attempts to infect and compromise more systems. As the collection of infected systems grows, it forms a network of bots, or a botnet.
How a botnet works –
Botnets are controlled by a master who has remote access and control of all the bots in a botnet. The botnet controller creates a command and control (C&C) site or uses Internet Relay Chat, an instant messaging protocol to issue commands to the bots in the net.
……………….
You can download the complete version of HP white paper here
